What is CMMC?
The Cybersecurity Maturity Model Certification is a cybersecurity compliance certification designed to strengthen and protect the supply chain of the Department of Defense and its vendors. The CMMC framework was created by the DoD in response to rising criminal cyber activity costing the U.S. economy between $57 billion and $109 billion in 2016 alone. The DoD has designed the CMMC framework to serve as a best practices guide for protecting Federal Contract Information or FCI and Controlled Unclassified Information or CUI.
By the DoD’s definition, these are defined as:
Federal Contract Information (FCI): FCI is information provided by or generated for the Government under contract not intended for public release.
Controlled Unclassified Information (CUI): is information that requires safeguarding or dissemination controls pursuant to and consistent with laws, regulations, and government-wide policies, excluding information that is classified under Executive Order 13526, Classified National Security Information, December 29, 2009, or any predecessor or successor order, or Atomic Energy Act of 1954, as amended.
The CMMC model uses the basic safeguarding requirements for FCI as the Federal Acquisition Regulation (FAR) Clause 52.204-21 and the security requirements for CUI as specified in NIST 800-171 / DFARS.
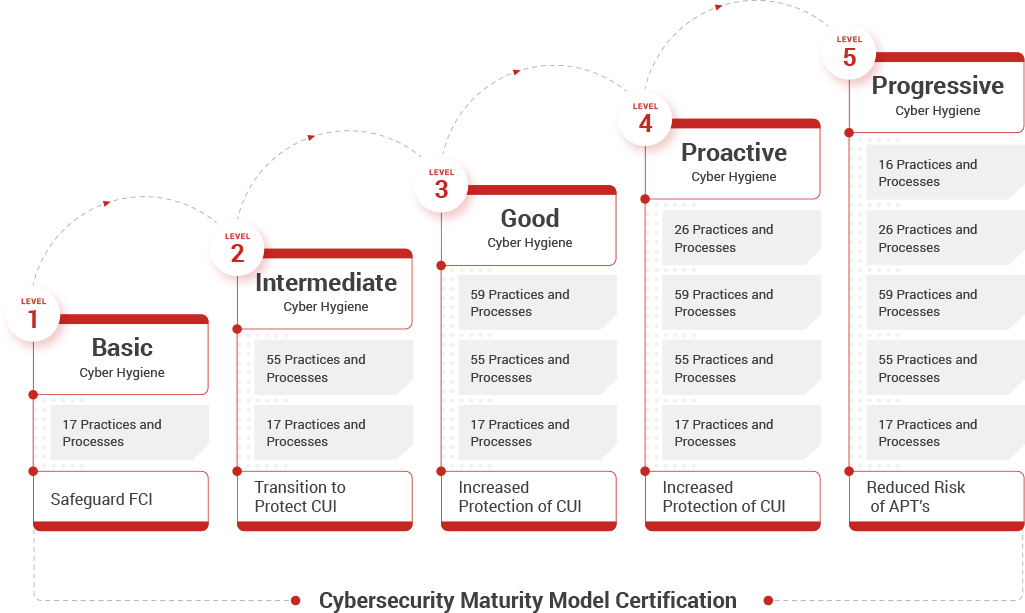
The Five Certification Levels of CMMC
The CMMC measures cybersecurity maturity with five levels and aligns a set of processes and practices with the type and sensitivity of the information to be protected and the associated range of threats.
Level 1: Safeguard Federal Contract Information (FCI)
Level 2: Serve as a transition step in cybersecurity maturity progression to protect CUI.
Level 3: Protect Controlled Unclassified Information
Level 4-5: Protect CUI and reduce risk of Advanced Persistent Threats
These levels of certification are achieved by Processes and Practices as defined in the CMMC.
CMMC Level 1 Requirements
CMMC Level 1 focuses on basic cyber hygiene and consists of the safeguarding requirements specified in 48 CFR 52.204-21. The Level 1 practices establish a foundation for the higher levels of the model and must be completed by all certified organizations. Not every domain within CMMC has Level 1 practices. At both this level and Level 2, organizations may be provided with FCI. FCI is information not intended for public release. It is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government. FCI does not include information provided by the Government to the public. While practices are expected to be performed, process maturity is not addressed at CMMC Level 1, and therefore, a CMMC Level 1 organization may have limited or inconsistent cybersecurity maturity processes.
CMMC Level 2 Requirements
2
CMMC Level 3 Requirements
3
CMMC Level 4 Requirements
4
CMMC Level 5 Requirements
5
CMMC Domains
CMMC consists of 17 domains with the majority originating from the Federal Information Processing Standards (FIPS) and NIST 800-171. CMMC includes three additional domains not included in those standards.
- Access Control (AC)
- Asset Management (AM)
- Audit and Accountability (AU)
- Awareness and Training (AT)
- Configuration Management (CM)
- Identification and Authentication (IA)
- Incident Response (IR)
- Maintenance (MA)
- Media Protection (MP)
- Personnel Security (PS)
- Physical Protection (PE)
- Recovery (RE)
- Risk Management (RM)
- Security Assessment (CA)
- Situational Awareness (SA)
- System and Communications Protection (SC)
- System and Information Integrity (SI)
CMMC ascribes 173 points across these 17 families and assigns them to the 5 levels accordingly.
What is our approach to compliance?
1
Compliance Audit
Our team conducts a series of interviews and a network audit to determine data access and usage.
2
Gap Analysis
A Gap Analysis identifies the missing pieces necessary to achieve compliance.
3
Remediation Plan
A remediation plan is put forth and executed with action steps towards compliance based on priority level.
4
Management
Infonaligy then monitors system usage and provides the service and support to maintain compliance.

